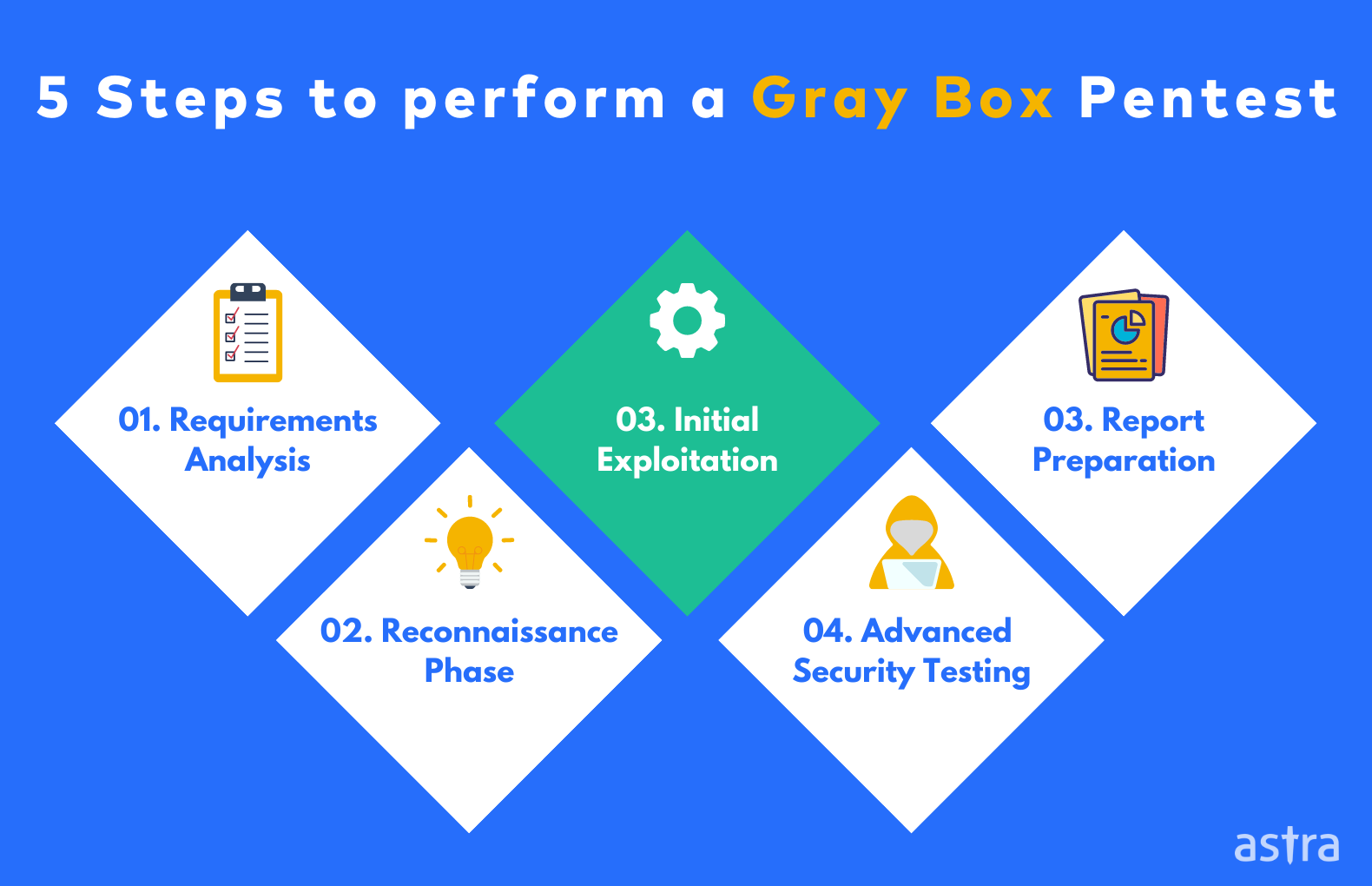
In the realm of cybersecurity, safeguarding sensitive data and systems is paramount. One crucial method for assessing and bolstering defenses is penetration testing, a simulated cyberattack designed to identify vulnerabilities before malicious actors can exploit them. Unlike black box testing, where testers have no prior knowledge of the system, or white box testing, where they have complete access, gray box penetration testing offers a balanced approach. This method provides testers with partial knowledge of the system’s internal structure, code, and architecture, allowing for a more targeted and efficient security assessment. Gray box penetration testing provides a practical and cost-effective means of identifying and mitigating potential security risks.
Understanding Gray Box Penetration Testing
Gray box penetration testing, also known as translucent box testing, occupies the middle ground in the spectrum of penetration testing methodologies. It’s a strategic approach where the tester has limited or partial knowledge of the target system. This knowledge typically includes:
- Network diagrams
- User roles and privileges
- Documentation of the system’s architecture
- Partial access to code
This partial knowledge allows the tester to focus their efforts on specific areas of concern, simulating a more realistic attack scenario where an attacker might have already gained some insider information. This could be through social engineering, compromised credentials, or other means.
Benefits of Gray Box Testing
More Efficient Testing: Partial knowledge allows testers to focus on specific areas, saving time and resources.
Realistic Attack Simulation: Mimics real-world scenarios where attackers may have some internal knowledge.
Improved Vulnerability Identification: Enables testers to identify vulnerabilities that might be missed by black box or white box testing alone.
Cost-Effective: The focused approach can reduce the overall cost of penetration testing.
Better Understanding of Security Posture: Provides a more comprehensive view of the system’s security strengths and weaknesses.
Gray Box vs. Black Box vs. White Box
Understanding the differences between these testing methodologies is crucial for selecting the right approach for your organization’s needs.
| Testing Type | Knowledge Level | Focus | Advantages | Disadvantages |
|---|---|---|---|---|
| Black Box | No prior knowledge | External vulnerabilities | Unbiased perspective, simulates external attacker | Can miss internal vulnerabilities, time-consuming |
| Gray Box | Partial knowledge | Both external and internal vulnerabilities | Efficient, realistic, balanced approach | Requires some level of internal documentation |
| White Box | Full knowledge | Internal vulnerabilities, code analysis | Comprehensive, identifies deep-seated issues | Can be time-consuming, may not simulate real-world attacks |
FAQ: Gray Box Penetration Testing
Q: What kind of information is typically provided to a gray box tester?
A: User roles and privileges, network diagrams, internal documentation, and sometimes partial access to code.
Q: Is gray box testing more expensive than black box testing?
A: Not necessarily. While it may require some initial effort to provide the tester with partial knowledge, the focused approach can often lead to a more efficient and cost-effective testing process.
Q: When is gray box testing the best choice?
A: When you want a balanced approach that simulates a realistic attack scenario and identifies both external and internal vulnerabilities.
Q: Who typically performs gray box penetration testing?
A: Security consultants or internal security teams with experience in penetration testing and a good understanding of the target system.
Ultimately, the choice of penetration testing methodology depends on your specific needs and objectives. However, gray box penetration testing offers a valuable middle ground, providing a realistic and efficient way to assess your organization’s security posture. By providing testers with partial knowledge, you can gain a more comprehensive understanding of your vulnerabilities and take proactive steps to mitigate potential risks.
In the realm of cybersecurity, safeguarding sensitive data and systems is paramount. One crucial method for assessing and bolstering defenses is penetration testing, a simulated cyberattack designed to identify vulnerabilities before malicious actors can exploit them. Unlike black box testing, where testers have no prior knowledge of the system, or white box testing, where they have complete access, gray box penetration testing offers a balanced approach. This method provides testers with partial knowledge of the system’s internal structure, code, and architecture, allowing for a more targeted and efficient security assessment. Gray box penetration testing provides a practical and cost-effective means of identifying and mitigating potential security risks.
Gray box penetration testing, also known as translucent box testing, occupies the middle ground in the spectrum of penetration testing methodologies. It’s a strategic approach where the tester has limited or partial knowledge of the target system. This knowledge typically includes:
- Network diagrams
- User roles and privileges
- Documentation of the system’s architecture
- Partial access to code
This partial knowledge allows the tester to focus their efforts on specific areas of concern, simulating a more realistic attack scenario where an attacker might have already gained some insider information. This could be through social engineering, compromised credentials, or other means.
More Efficient Testing: Partial knowledge allows testers to focus on specific areas, saving time and resources.
Realistic Attack Simulation: Mimics real-world scenarios where attackers may have some internal knowledge.
Improved Vulnerability Identification: Enables testers to identify vulnerabilities that might be missed by black box or white box testing alone.
Cost-Effective: The focused approach can reduce the overall cost of penetration testing.
Better Understanding of Security Posture: Provides a more comprehensive view of the system’s security strengths and weaknesses.
Understanding the differences between these testing methodologies is crucial for selecting the right approach for your organization’s needs.
| Testing Type | Knowledge Level | Focus | Advantages | Disadvantages |
|---|---|---|---|---|
| Black Box | No prior knowledge | External vulnerabilities | Unbiased perspective, simulates external attacker | Can miss internal vulnerabilities, time-consuming |
| Gray Box | Partial knowledge | Both external and internal vulnerabilities | Efficient, realistic, balanced approach | Requires some level of internal documentation |
| White Box | Full knowledge | Internal vulnerabilities, code analysis | Comprehensive, identifies deep-seated issues | Can be time-consuming, may not simulate real-world attacks |
Q: What kind of information is typically provided to a gray box tester?
A: User roles and privileges, network diagrams, internal documentation, and sometimes partial access to code.
Q: Is gray box testing more expensive than black box testing?
A: Not necessarily. While it may require some initial effort to provide the tester with partial knowledge, the focused approach can often lead to a more efficient and cost-effective testing process.
Q: When is gray box testing the best choice?
A: When you want a balanced approach that simulates a realistic attack scenario and identifies both external and internal vulnerabilities.
Q: Who typically performs gray box penetration testing?
A: Security consultants or internal security teams with experience in penetration testing and a good understanding of the target system.
Ultimately, the choice of penetration testing methodology depends on your specific needs and objectives. However, gray box penetration testing offers a valuable middle ground, providing a realistic and efficient way to assess your organization’s security posture. By providing testers with partial knowledge, you can gain a more comprehensive understanding of your vulnerabilities and take proactive steps to mitigate potential risks.