Radio-Frequency Identification (RFID) technology has revolutionized various industries‚ from supply chain management to access control. However‚ the widespread adoption of RFID has also introduced a new set of security vulnerabilities and threats that must be addressed. Understanding these potential risks is crucial for organizations seeking to implement RFID systems securely and effectively. This article delves into the top 10 RFID security concerns and threats‚ providing insights into the challenges and offering potential mitigation strategies.
Understanding RFID Security Risks
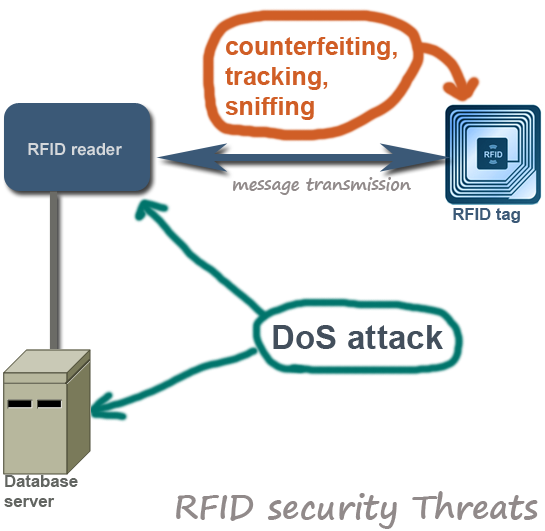
RFID systems‚ by their very nature‚ are susceptible to various security breaches. The wireless communication between the tag and the reader creates opportunities for malicious actors to intercept‚ manipulate‚ or even disable the system. The lack of strong encryption and authentication mechanisms in some RFID implementations further exacerbates these vulnerabilities.
Common RFID Attack Vectors
- Eavesdropping: Intercepting communication between the tag and the reader to steal sensitive data.
- Cloning: Creating a duplicate of an RFID tag to gain unauthorized access or impersonate a legitimate user.
- Spoofing: Transmitting false data to the reader to disrupt operations or manipulate information.
- Denial-of-Service (DoS): Overwhelming the RFID system with requests to render it unusable.
- Tag Killing: Permanently disabling an RFID tag‚ rendering it useless.
- Data Theft: Unauthorized access to sensitive data stored on RFID tags.
- Counterfeiting: Using cloned RFID tags to create counterfeit products or gain unauthorized access.
- Privacy Violations: Tracking individuals or objects without their knowledge or consent.
- Replay Attacks: Capturing and retransmitting valid RFID signals to gain unauthorized access.
- Man-in-the-Middle Attacks: Intercepting and manipulating communication between the tag and the reader.
- Tag Tampering: Physically altering or damaging RFID tags to disrupt operations.
- Side-Channel Attacks: Exploiting physical characteristics of RFID devices to extract sensitive information.
- Firmware Exploitation: Exploiting vulnerabilities in the RFID reader or tag firmware to gain control of the system.
- Lack of Authentication: Weak or non-existent authentication mechanisms allowing unauthorized access.
- Denial of Service: Overloading the RFID system to prevent legitimate users from accessing it.
Mitigation Strategies
Addressing these security concerns requires a multi-faceted approach‚ including:
- Strong Encryption: Implementing robust encryption algorithms to protect data transmitted between the tag and the reader.
- Mutual Authentication: Verifying the identity of both the tag and the reader before allowing communication.
- Access Control: Restricting access to RFID data and functionalities based on user roles and permissions.
- Physical Security: Protecting RFID tags and readers from physical tampering and theft.
- Regular Security Audits: Conducting regular security assessments to identify and address vulnerabilities.
FAQ: RFID Security
What is the biggest security risk associated with RFID?
Data theft and privacy violations are often cited as the biggest security risks‚ as they can lead to significant financial losses and reputational damage.
How can I protect my RFID system from attacks?
Implementing strong encryption‚ mutual authentication‚ and access control measures are crucial steps in protecting your RFID system.
Are all RFID systems vulnerable to security threats?
While all RFID systems have some inherent vulnerabilities‚ the level of risk depends on the specific implementation and the security measures in place.
What is tag cloning and how can I prevent it?
Tag cloning involves creating a duplicate of an RFID tag. Using strong encryption and authentication protocols can help prevent tag cloning.
The Future of RFID Security
The landscape of RFID security is constantly evolving‚ driven by advancements in both technology and attack techniques. As RFID becomes more integrated into critical infrastructure and everyday life‚ the need for robust security measures will only intensify. Future trends in RFID security include:
- Advanced Encryption Techniques: Development and implementation of more sophisticated encryption algorithms to counter evolving attack methods.
- AI-Powered Threat Detection: Utilizing artificial intelligence and machine learning to identify and respond to anomalous RFID activity in real-time.
- Blockchain Integration: Leveraging blockchain technology to enhance the security and integrity of RFID data.
- Standardization and Certification: Establishing industry-wide standards and certification programs to ensure consistent security practices.
- Quantum-Resistant RFID: Exploring the potential of quantum-resistant cryptography to protect RFID systems from future quantum computing threats.
Comparative Table: RFID Security Measures
| Security Measure | Description | Benefits | Limitations |
|---|---|---|---|
| Encryption | Encoding data to prevent unauthorized access. | Protects data confidentiality. | Can be computationally expensive. |
| Authentication | Verifying the identity of the tag and reader. | Prevents unauthorized access. | Can be vulnerable to replay attacks if not implemented correctly. |
| Access Control | Restricting access to RFID data based on user roles. | Limits the impact of a security breach. | Requires careful configuration and management. |
| Physical Security | Protecting RFID tags and readers from physical tampering. | Prevents physical attacks. | Can be costly to implement. |
Staying Ahead of the Curve
Maintaining a strong security posture in the face of evolving RFID threats requires a proactive and adaptive approach. Organizations should:
- Stay Informed: Keep abreast of the latest RFID security vulnerabilities and best practices.
- Implement a Security-First Approach: Integrate security considerations into every stage of the RFID system lifecycle‚ from design to deployment.
- Train Employees: Educate employees about RFID security risks and best practices.
- Regularly Update Systems: Apply security patches and updates to RFID readers and tags promptly.
- Monitor RFID Activity: Continuously monitor RFID systems for suspicious activity and respond promptly to any incidents.
The ongoing development and refinement of security protocols are crucial for ensuring the long-term viability and trustworthiness of RFID technology. By prioritizing security and embracing innovation‚ we can unlock the full potential of RFID while mitigating the associated risks. As we move forward‚ a collaborative effort between researchers‚ industry professionals‚ and policymakers will be essential to address the evolving challenges and ensure a secure and reliable future for RFID applications. The future of secure RFID depends on our collective commitment to vigilance and proactive security measures.
Radio-Frequency Identification (RFID) technology has revolutionized various industries‚ from supply chain management to retail and healthcare. Its ability to wirelessly identify and track objects has led to increased efficiency and automation. However‚ this convenience comes with inherent security risks. Understanding the potential vulnerabilities of RFID systems is crucial for mitigating threats and ensuring data integrity. The following outlines the top 10 RFID security concerns and threats that organizations should be aware of‚ highlighting the importance of robust security measures to protect sensitive information and prevent unauthorized access. These concerns range from basic eavesdropping to sophisticated attacks that can compromise entire systems.
Top 10 RFID Security Concerns
- Eavesdropping: Intercepting communication between the tag and the reader to steal data.
- Cloning: Copying the data from a legitimate tag onto a counterfeit tag.
- Privacy Violations: Tracking individuals or objects without their knowledge or consent.
- Replay Attacks: Capturing and retransmitting valid RFID signals to gain unauthorized access.
- Man-in-the-Middle Attacks: Intercepting and manipulating communication between the tag and the reader.
- Tag Tampering: Physically altering or damaging RFID tags to disrupt operations.
- Side-Channel Attacks: Exploiting physical characteristics of RFID devices to extract sensitive information.
- Firmware Exploitation: Exploiting vulnerabilities in the RFID reader or tag firmware to gain control of the system.
- Lack of Authentication: Weak or non-existent authentication mechanisms allowing unauthorized access.
- Denial of Service: Overloading the RFID system to prevent legitimate users from accessing it.
Addressing these security concerns requires a multi-faceted approach‚ including:
- Strong Encryption: Implementing robust encryption algorithms to protect data transmitted between the tag and the reader.
- Mutual Authentication: Verifying the identity of both the tag and the reader before allowing communication.
- Access Control: Restricting access to RFID data and functionalities based on user roles and permissions.
- Physical Security: Protecting RFID tags and readers from physical tampering and theft.
- Regular Security Audits: Conducting regular security assessments to identify and address vulnerabilities.
Data theft and privacy violations are often cited as the biggest security risks‚ as they can lead to significant financial losses and reputational damage.
Implementing strong encryption‚ mutual authentication‚ and access control measures are crucial steps in protecting your RFID system.
While all RFID systems have some inherent vulnerabilities‚ the level of risk depends on the specific implementation and the security measures in place.
Tag cloning involves creating a duplicate of an RFID tag. Using strong encryption and authentication protocols can help prevent tag cloning.
The landscape of RFID security is constantly evolving‚ driven by advancements in both technology and attack techniques. As RFID becomes more integrated into critical infrastructure and everyday life‚ the need for robust security measures will only intensify. Future trends in RFID security include:
- Advanced Encryption Techniques: Development and implementation of more sophisticated encryption algorithms to counter evolving attack methods.
- AI-Powered Threat Detection: Utilizing artificial intelligence and machine learning to identify and respond to anomalous RFID activity in real-time.
- Blockchain Integration: Leveraging blockchain technology to enhance the security and integrity of RFID data.
- Standardization and Certification: Establishing industry-wide standards and certification programs to ensure consistent security practices.
- Quantum-Resistant RFID: Exploring the potential of quantum-resistant cryptography to protect RFID systems from future quantum computing threats.
| Security Measure | Description | Benefits | Limitations |
|---|---|---|---|
| Encryption | Encoding data to prevent unauthorized access. | Protects data confidentiality. | Can be computationally expensive. |
| Authentication | Verifying the identity of the tag and reader. | Prevents unauthorized access. | Can be vulnerable to replay attacks if not implemented correctly. |
| Access Control | Restricting access to RFID data based on user roles. | Limits the impact of a security breach. | Requires careful configuration and management. |
| Physical Security | Protecting RFID tags and readers from physical tampering. | Prevents physical attacks. | Can be costly to implement. |
Maintaining a strong security posture in the face of evolving RFID threats requires a proactive and adaptive approach. Organizations should:
- Stay Informed: Keep abreast of the latest RFID security vulnerabilities and best practices.
- Implement a Security-First Approach: Integrate security considerations into every stage of the RFID system lifecycle‚ from design to deployment.
- Train Employees: Educate employees about RFID security risks and best practices.
- Regularly Update Systems: Apply security patches and updates to RFID readers and tags promptly.
- Monitor RFID Activity: Continuously monitor RFID systems for suspicious activity and respond promptly to any incidents.
The ongoing development and refinement of security protocols are crucial for ensuring the long-term viability and trustworthiness of RFID technology. By prioritizing security and embracing innovation‚ we can unlock the full potential of RFID while mitigating the associated risks. As we move forward‚ a collaborative effort between researchers‚ industry professionals‚ and policymakers will be essential to address the evolving challenges and ensure a secure and reliable future for RFID applications. The future of secure RFID depends on our collective commitment to vigilance and proactive security measures.
Emerging Technologies and Their Impact on RFID Security
Beyond the immediate horizon‚ several emerging technologies promise to reshape the landscape of RFID security‚ both positively and negatively. Understanding these trends is crucial for organizations seeking to future-proof their RFID deployments. These technologies present both opportunities for enhanced security and new avenues for potential attacks.
The Rise of Lightweight Cryptography
As RFID technology permeates resource-constrained environments like wearable sensors and disposable medical devices‚ the need for lightweight cryptographic solutions becomes paramount. These algorithms are designed to provide strong security with minimal computational overhead‚ making them ideal for low-power RFID tags. However‚ the development and validation of these algorithms require careful scrutiny to ensure they are resistant to emerging attack vectors. The challenge lies in balancing security strength with resource efficiency.
The Double-Edged Sword of the Internet of Things (IoT)
The integration of RFID with the Internet of Things (IoT) creates a vast network of interconnected devices‚ offering unprecedented opportunities for data collection and automation. However‚ this interconnectedness also expands the attack surface‚ making RFID systems more vulnerable to remote exploitation. Securing RFID deployments within the IoT ecosystem requires a holistic approach that addresses vulnerabilities at all levels of the network stack. This includes securing the RFID tags themselves‚ the readers‚ the communication channels‚ and the backend servers.
The Potential of Physical Unclonable Functions (PUFs)
Physical Unclonable Functions (PUFs) offer a promising approach to enhancing RFID security by leveraging the inherent physical variations in manufacturing processes to create unique‚ unclonable identifiers for each tag. These identifiers can be used for authentication and key generation‚ making it significantly more difficult for attackers to clone or counterfeit RFID tags. However‚ the reliability and robustness of PUFs in harsh environments remain a concern‚ and further research is needed to address these challenges.
The Threat of Advanced Persistent Threats (APTs) Targeting RFID
As RFID becomes more critical to business operations‚ it is increasingly likely to become a target for Advanced Persistent Threats (APTs). These sophisticated attackers are highly skilled and well-resourced‚ and they are capable of launching complex‚ multi-stage attacks that can bypass traditional security measures. Defending against APTs requires a proactive and layered security approach that includes threat intelligence‚ intrusion detection‚ and incident response capabilities. Organizations must be prepared to detect and respond to sophisticated attacks that may target their RFID systems.